Do You Fasten Your Seatbelt On The Internet? The Story of Cyber Crime!

Some people don’t even fasten their seatbelts while driving, but in most cases this is a habit backed up by strict laws. Now let me ask you: do you behave the same when you go surfing (not in Hawaii, but on the Internet)?
According to the 2013 Norton Report, a significant amount of people doesn’t think about safety measures of their computers, smart-phones, and data. Is it because it is not enforced by law? Or are we simply not informed enough? I don’t have the power to enact laws (still) but I can put some data on the table. Because I believe that this is a big, developing problem and that safety measures should become a habit, just like fastening your seatbelt.
Cyber security has a scent of a scientific and official expression, while it is actually a part of our everyday lives; most of us apply at least some security measures to ensure integrity and confidentiality of our data, either at work or home. Furthermore, let’s see what lays behind the term cyber crime. Any crime that involves a computer and a network is a cyber crime, where computer may be a tool or a target itself. Usually, when we talk about crimes against individuals, computer is considered as a tool to take advantage of human weaknesses online. You have been a victim of cyber crime if you experienced some of the following: stalking, bullying, fraud, spam emails, viruses or hacking.
So what is the scope of the problem globally?
You can find a lot of interesting data concerning Internet threats and cyber security in the press kits of Symantec. 2013 Norton report (global survey of end-users) is an annual research conducted by Symantec, digging into the dangers and financial costs of the cyber crime, as well as the dangerous behaviors of Internet consumers, which makes them vulnerable online.
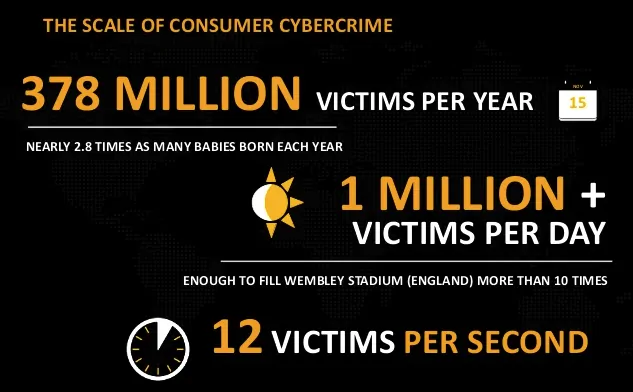
It’s time to face some worrying numbers: there are 378 million victims of cyber crime per year, which is more than 1 million victims per day, or 12 victims per second. If we stop and do some math, this means that by the time you read this post, there will be around 3600 more victims worldwide. Which is why I hope, by the time you read this post, you will check if your device is adequately protected against malware.
If this is not argumentative enough for you, then let me tell you that 50% of online adults have been victims or experienced negative online situations in 2012. Examples vary from receiving nude images from strangers to being stalked or bullied online. 41% of online adults have fallen victim to attacks such as viruses, hacking, malware, scams and theft. For me, this is argumentative enough to say that both dangers and victims online are numerous and that lack of awareness and precaution of one group is used largely by the other group.
Do smart-phone and tablet users behave smart?
Our devices are previous to us. We keep them at our reach even while sleeping, but do we secure the data we store in them? According to the data, we do think about safety of our PC’s, but the situation is different when it comes to securing smart-phones and tablets. Almost half of smart-phone and tablet users don’t use basic security measures like passwords, security software or back up files, and even more worrying – 57% of mobile device users aren’t aware that security solutions EXIST. If you are reading this and don’t feel affected because you use security software with advanced protection, then you have a reason to feel special today – only one quarter of users does the same.
On the other hand, if you are reading this and thinking that there isn’t a significant number of mobile cybercrimes, then you might be surprised: 38% of mobile users had already experienced mobile cybercrime, while one quarter has lost their device or had it stolen.
Sharing is caring?
Do you check your Facebook/Twitter first thing in the morning? I do the same, and we are not alone at it – 25% of social media users check their social network within 15 minutes of waking up! No problem, we strive for information/likes/discussions from dusk till dawn, but we need to avoid some risky behaviors:
– 39% of users don’t log out after each session
– One quarter of social media users share their passwords with others
– One third connects with people they don’t know
When was the last time you created a photo album…offline? When was the last time you sent a letter or a postcard via post? When you communicate to people on daily basis, what do you use? What happens is that nowadays, our photos and communication data are stored in our devices, and on our social media profiles or applications such as Viber, Messenger, Whatsapp… Your social media profile is private, as is your bag or jeans pocket, so take care about your passwords and whom you connect to!
Now, if I scared you a little bit, I don’t want you to leave with that emotion, but with some useful tips from Symantec:
– Defend your data with an all-inclusive security suite which will protect you against online dangers and don’t forget to include all your devices: lap top, tablets, smart-phones
– Think of your smart-phones as mini-computers because these are the fastest-growing targets for cybercriminals
Protect your data, your desktop, and your server. Protect your virtual self, for it has become equally important as things you keep physically in your home. Passwords, log out, antivirus and other security mechanisms are your seat belts, so you might as well secure that you can enjoy your ride. 🙂
More info about this issue can be found here. Also, here is interesting infographic with data from the research.
We are going to be writing more about cyber security and means by which you can protect yourself online, so make sure to follow our blog!