What is DNSSEC and Why Should You Care About It
As Internet users, we’ve developed certain online habits. We get emotionally attached to certain blogs and various types of media we consume daily. Reading through our news feed first thing in the morning has become an instinct. And regardless of the way we access desired content, directly or over search engines – we expect the website we are looking for to magically appear on our screen.
Except it’s not magic.
Given the fact we operate in one single global cyberspace called the Internet, the address of each website is completely unique. Wondering who coordinates these unique addresses?
We already wrote about how domain names work, but here’s a brief reminder: People communicate through words, while computers understand only numbers. When you type in the domain name of the website you want to visit, it has to be translated into a number by a specific system. So, in order for the connection to get established – these names have to be translated to numeric equivalent, i.e. IP addresses. The system that makes this happen is called Domain Name System (DNS). It is also known as the phone book of the Internet as it tells computers the exact location of the websites (or another type of services) and shows them where to send a request and retrieve information. As you can see from this, before the website appears on your screen, your computer first has to figure out where is the website by asking DNS to translate the name into a number (a domain name into an IP address).
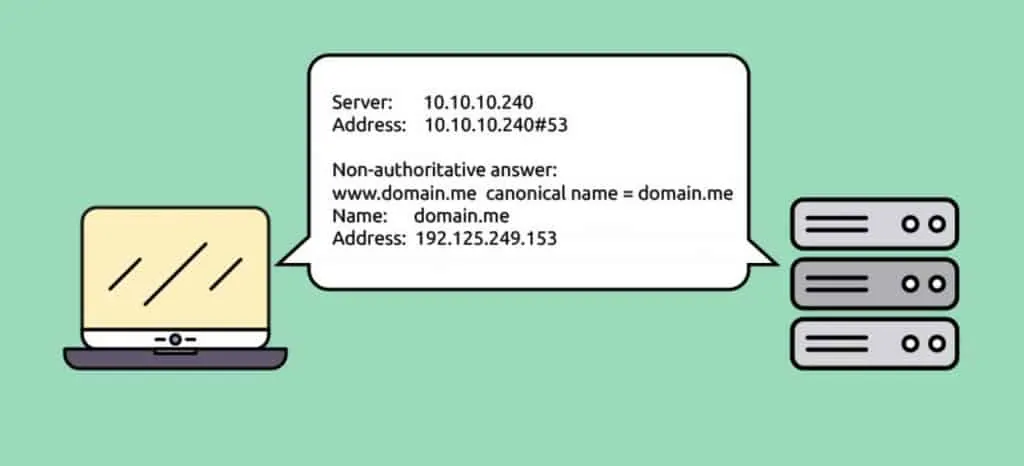
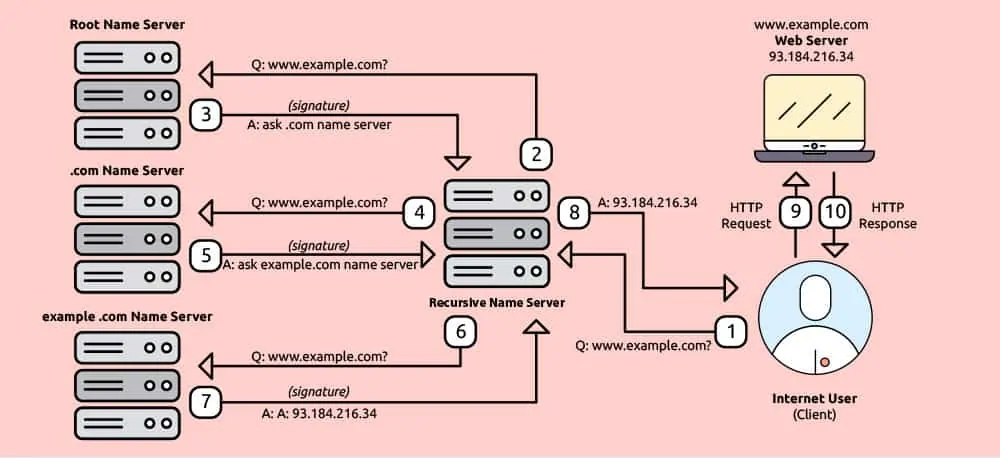
But let’s focus on this communication between your computer and the DNS server. It is a non-encrypted conversation where your computer sends a request for translation of the requested domain name into a number. For example www.domain.me translates into 192.124.249.153. This is how it looks like:
The IP address of the DNS server – 10.10.10.240 (all devices on the internet have an IP address) – tells your computer that the www.domain.me web site is at the 192.124.249.153 IP address.
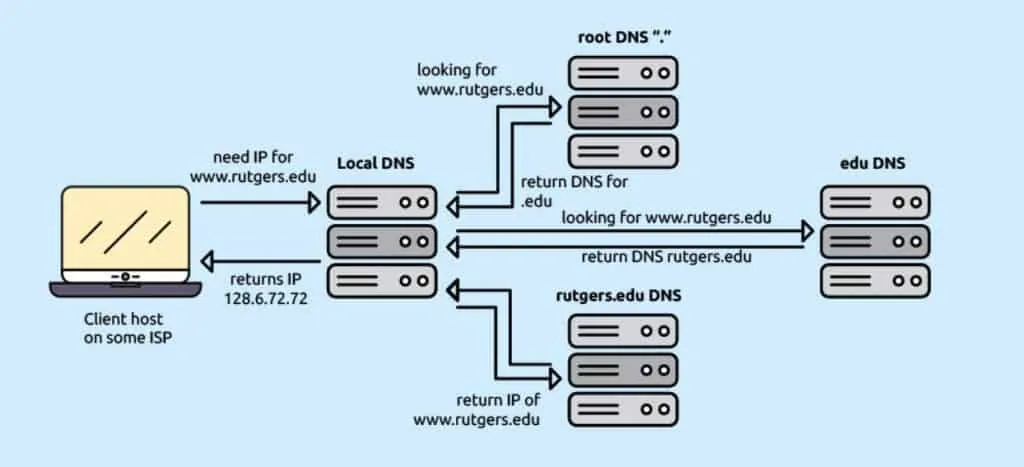
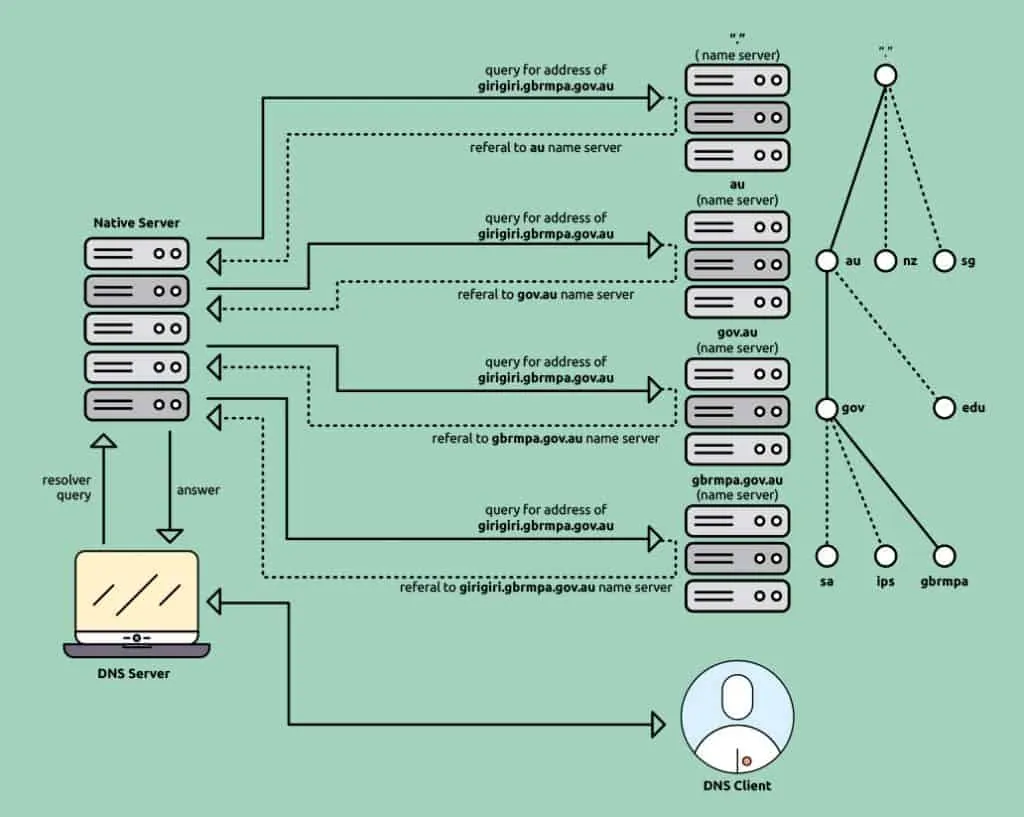
Of course, this is simplified. Basically, if the domain name server your computer first asks doesn’t know what is the IP address of the website www.domain.me it has to ask another domain name server, and then it stores the information for future use. We will get just a bit more technical here for clarity’s sake:
Domain names are organised in a hierarchical structure. This is how it works on the example of www.domain.me: The ROOT server (located at the public IP location) is at the top of the pyramid and it knows where the top level extension servers are, ie. it answers
The problem with the DNS conversation is that it can get intercepted without your computer knowing where the answer is coming from – it is not able to verify who gave the answer. That’s where a layer of security steps in: Domain Name System Security Extensions (DNSSEC).
Read more: How to Setup DNSSEC
Explaining DNSSEC
In July 2008, Dan Kaminsky announced that he had discovered a fundamental flaw in the Domain Name System (DNS) protocol. He found out that a person with bad intents can set up a domain name server, listen to a DNS conversation, configure a DNS server for whatever site he or she wanted and start answering with wrong IP addresses. This is called DNS spoofing:
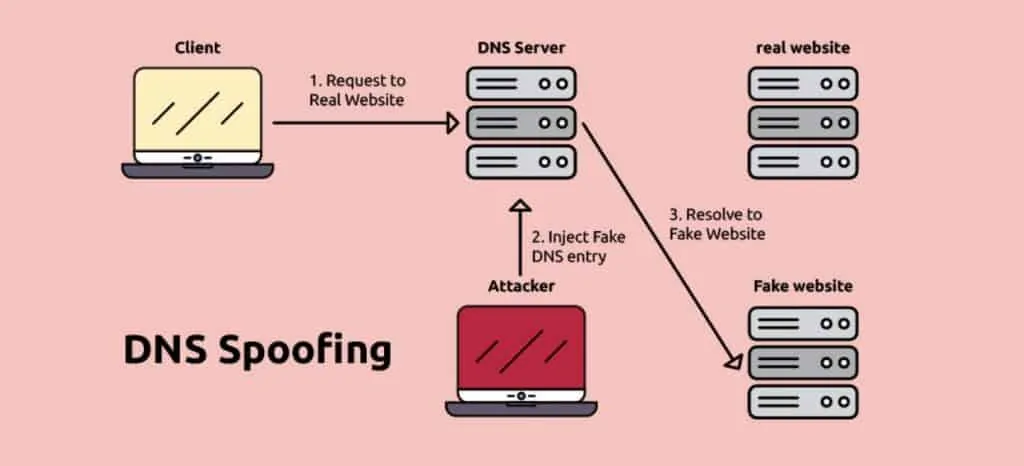
This means that somebody could lead you to open a site you think is regular and maybe type in your username, password, credit card number etc. And you would not even know that a site is fake.
The CERT Coordination Center together with Dan Kaminsky proposed DNSSEC as a way to bring assurance to answers provided by DNS. In July 2010 ICANN published the signed ROOT zone, making DNSSEC functional and available on ROOT DNS.
DNSSEC makes these answers authentic by digitally signing answers. Note that the responses are signed so your computer can check who is it getting the answer from. That way, you are protected and sure that the website on your screen is actually the website you wanted to open.
To find out how it really works read on!
How DNSSEC Works
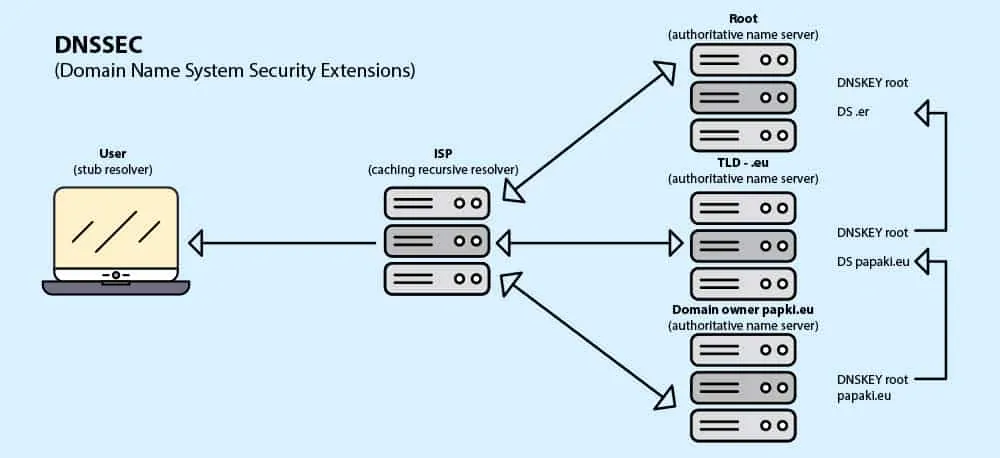
DNSSEC protects you (and the internet community) by using a public key cryptography for digitally signing authoritative zone data and validating its destination.
It means that, on our example, “www.domain.me” the response that comes to your computer from the root name server on the question (where is .ME name server) includes a signature key from
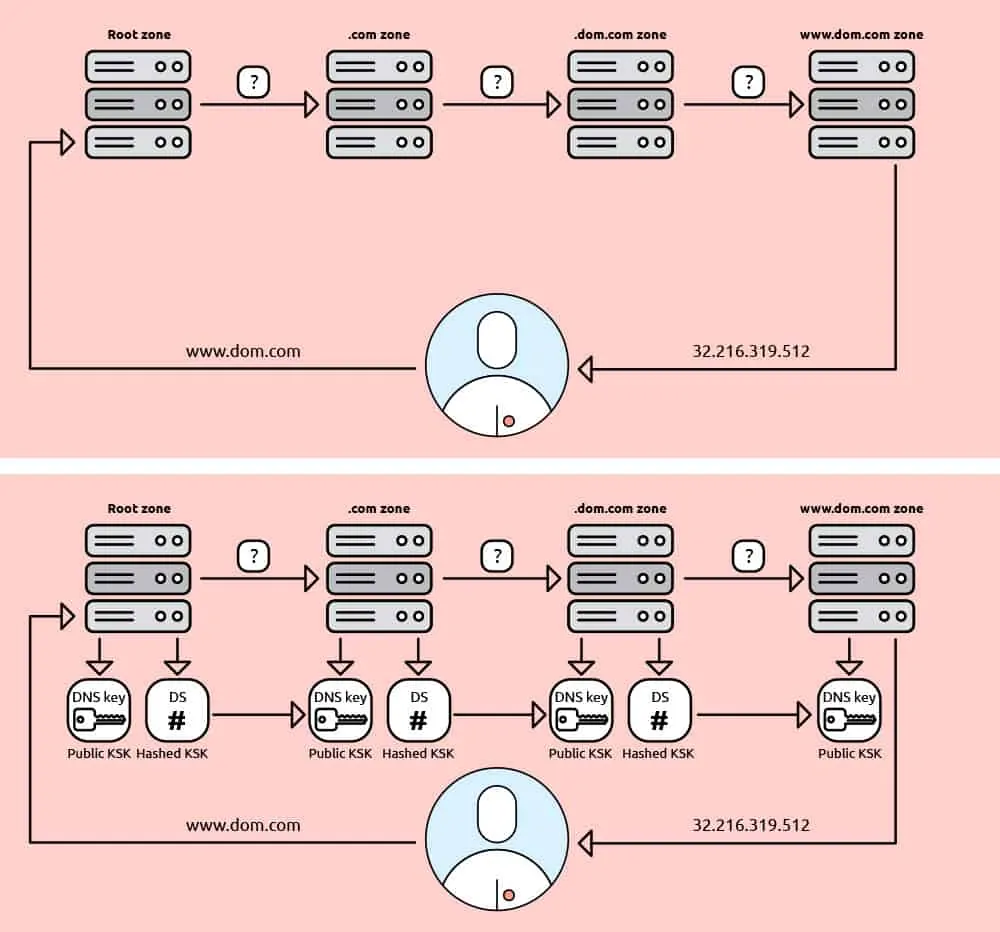
To ensure everything runs smoothly, the first root zone servers were signed by ICANN, the most authoritative entity on the internet, and then every top level domain (TLD) operator did the same for their own extension. .ME registry
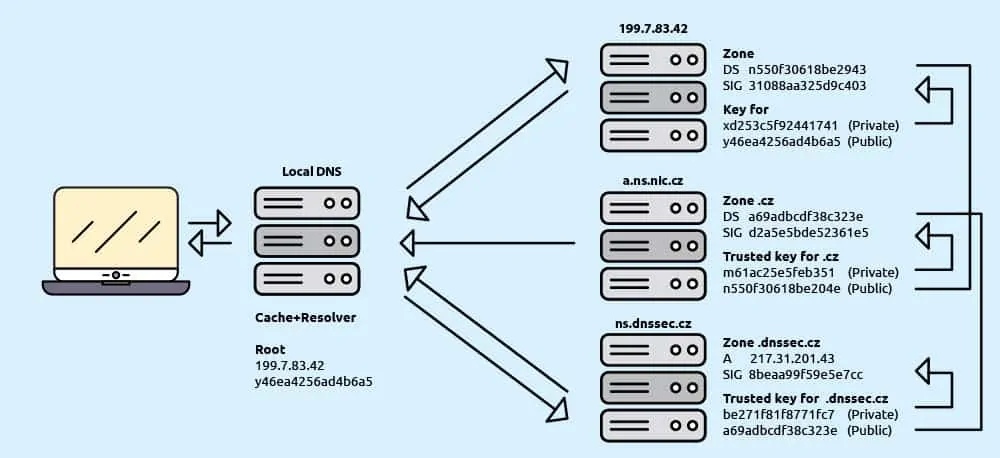
Basically, when you type a domain name or you are redirected by a search engine, your computer sends a request for translation to DNS server that accepts this request, but it also requests the DNSSEC key for authentication. Only when the key is received, compared and verified (confirmed that they are identical), your computer has an official confirmation that everything’s a-ok and the user is directed to the desired website. This validation step is crucial: if the key doesn’t match the key one level above (that is already verified), the website will not open.
Because of this extra layer of security, we can expect a decline in successful phishing attempts via DNS spoofing as with DNSSEC – users will not be redirected to malicious websites.
Just like with any security measure, DNSSEC has to continue evolving. One of the planned changes for increased safety is the Key Signing Key Rollover. Simply put, it implies a better security practice of regularly scheduled
However, ICANN has announced its plans to postpone this change of the cryptographic key, since it has identified possible issues with the resolvers who do not monitor and accept this change, which would lead them into serious problems. All the answers from the root name system would be treated as unverified, so the part of the internet they serve would stop working.
